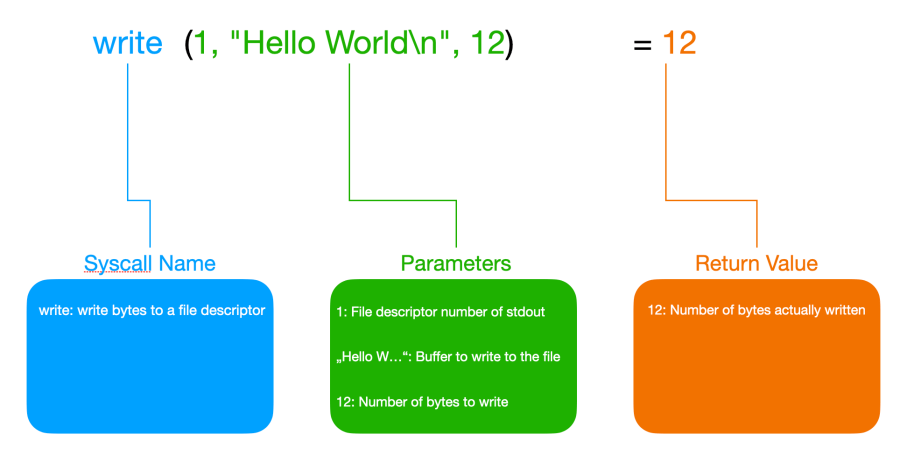
Tracing a program with strace generates a lot of output because of the sheer number of syscalls every program calls during its runtime. This can become overwhelming very quickly, making it hard to analyze the trace and find what you are looking for.
Fortunately, strace has several features that allow you to limit which syscalls it actually traces.
Limiting by Name
The simplest mechanism to limit the number of traced syscalls is by specifying the name of one syscall you want to trace. To do this, you can use the -e flag followed by trace= and the name of the syscall. In this example we trace the /bin/ls program and we only want strace to report the openat syscalls executed by the program:
$ strace -e trace=openat /bin/ls
This should give you an output similar to this:
Continue reading “Limiting which Syscalls to Trace with Strace”